In recent weeks, underground forums on the dark web have continued to flourish as bustling marketplaces where cybercriminals sell unauthorized access to corporate networks. From VPN credentials to Remote Desktop Protocol (RDP) access, threat actors take advantage of compromised corporate environments, often leveraging data from recent breaches or stolen via infostealers. This analysis highlights the trends observed in the last few weeks, shedding light on the types of actors involved, the most targeted countries and sectors, and the types of access being traded.
Selling Access to Corporate Networks Through Key Actors on Underground Forums
In just the last few weeks, over 250 distinct threat actors have been identified on underground forums, all involved in selling access to corporate networks. These actors can be divided into two major categories:
- Individual cybercriminals – Typically specializing in phishing attacks or leveraging malware like infostealers, these individuals focus on lower-value or opportunistic attacks.
- Organized cybercrime groups – These structured groups act as access brokers, offering extensive credential dumps and long-term, persistent access to corporate environments. Their capabilities are far more advanced, often involving sophisticated breaches and after-sale services to ensure buyers can maximize the value of the access.
Breakdown of Threat Actors:
- 60% of the identified actors are individuals, concentrating on smaller, low-value targets, often selling low-risk access points.
- The remaining 40% are part of coordinated cybercriminal groups, focusing on high-value targets with comprehensive access that often includes post-sale support like lateral movement within networks and privilege escalation.
These actors don’t just stop at initial access. A significant number of them provide additional services, such as helping buyers navigate through compromised corporate systems and avoid detection. The after-sale support offered by these groups often includes technical assistance to move laterally within the network and maintain persistent access, ensuring attackers can continue exploiting their entry points over time.
The data from just a few weeks offers a window into the vast and diverse ecosystem of cybercrime thriving on underground forums. This highlights the rapidly evolving nature of these threat actors and underscores the need for corporations to stay vigilant against an ever-growing array of cyber threats.
The persistent activity observed emphasizes the continuous development of more advanced methods to breach and exploit corporate environments, making it clear that cybersecurity must remain a top priority for organizations across all sectors.
Most Targeted Countries
Recent data from underground forums shows that threat actors are targeting companies and institutions across multiple continents, with a clear focus on high-value sectors like finance, technology, government, and energy. Here’s a summarized breakdown of the affected countries and continents:
North America
- United States: Primarily targets in the financial and technology sectors.
- Canada: Focus on financial and real estate sectors.
- Mexico: Targets include government agencies and financial services.
Europe
- Russia: Focus on energy and government sectors.
- Poland: Targets in the manufacturing sector.
- United Kingdom: Primarily financial services and wealth management.
Asia
- Israel: Focus on finance and technology sectors.
- Japan: Targets in educational and technology firms.
- India: Significant focus on IT and outsourcing sectors.
South America
- Brazil: Targets in the financial and government sectors.
Middle East
- Iran: Focus on educational institutions.
Africa
- South Africa: Limited but significant interest in the financial sector.
Recent Data Trends in Cybercriminal Targeting & Selling Access to Corporate Networks
The latest data from underground forums indicates a growing focus on three main sectors: finance, education, and real estate. These sectors are increasingly becoming targets for cybercriminals, primarily due to the wealth of sensitive information they hold and their operational importance.
Finance Sector
Access to financial services firms has become one of the most common offerings on underground forums. Financial institutions are especially vulnerable because they manage vast amounts of sensitive data, from customer information to transaction details. This data is not only valuable for direct financial gain but also for long-term exploitation, such as fraud and identity theft.
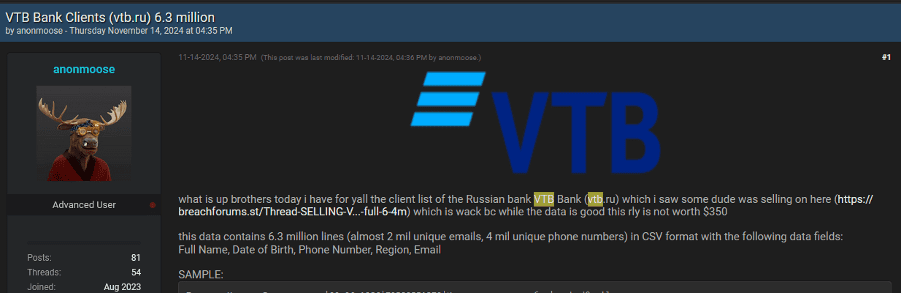
Threat actors are selling access to financial organizations, particularly banks and investment firms, that control billions in assets. These listings often include VPN and RDP access to corporate networks, allowing attackers to infiltrate the system and potentially deploy ransomware or steal sensitive data. Cybercriminal groups see this as a high-return opportunity, especially since financial institutions are often willing to pay ransoms to recover their operations quickly.
Education Sector
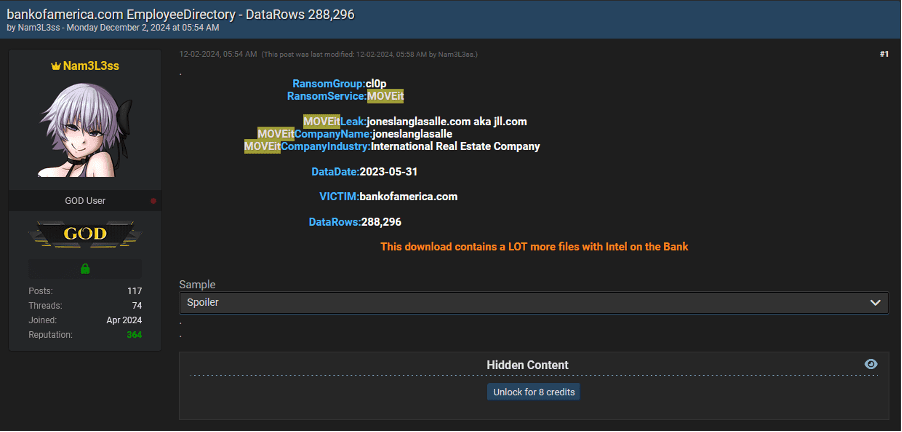
Educational institutions, particularly large universities with many employees and students, are becoming frequent victims of cyberattacks, especially ransomware. Schools and universities hold sensitive intellectual property, personal student data, and research information, making them attractive targets. Attackers frequently exploit this data by using stolen credentials obtained from phishing or malware campaigns. Once inside, they can lock down critical systems and demand a ransom, often crippling educational services and access to essential resources.
This rise in attacks on educational institutions aligns with the broader trend of ransomware-as-a-service (RaaS), where organized cybercriminal groups offer ransomware to affiliates, who then launch attacks and split the ransom payments. Educational institutions, especially those involved in cutting-edge research or government-sponsored projects, are prime targets for these sophisticated, high-impact ransomware campaigns.
Real Estate Sector
The real estate sector is another emerging target for cybercriminal groups, with listings for real estate firms becoming more common. These companies hold critical data on property ownership, transactions, and financial dealings, making them attractive to attackers seeking to steal valuable information or disrupt operations. The real estate industry also relies on secure networks to manage large transactions and sensitive communications, further making it a target for ransomware and data exfiltration.
Ransomware-as-a-Service (RaaS) Influence
Organized cybercriminal groups are increasingly using RaaS to monetize stolen data. This model allows cybercriminals to sell access or share ransomware tools with affiliates who conduct the attacks, splitting profits with the developers of the ransomware. The shift toward this model has lowered the barrier to entry for cybercriminals, allowing even low-skilled attackers to participate in high-impact attacks. Institutions in the finance, education, and real estate sectors are prime targets for RaaS-based attacks because of the high potential for extortion, intellectual property theft, and operational disruption.
Overall, the convergence of RaaS with sector-specific targeting demonstrates how organized cybercrime is evolving, with specialized groups focusing on high-value sectors that are more likely to pay ransoms or suffer significant disruptions from attacks.
Links to Public Breaches and Infostealers
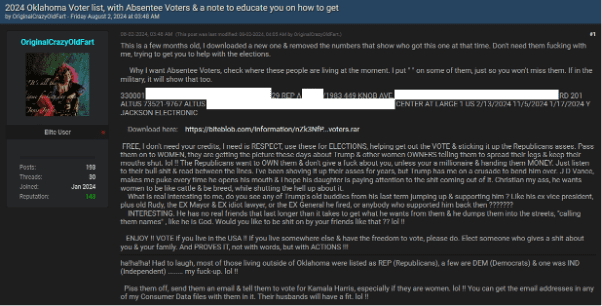
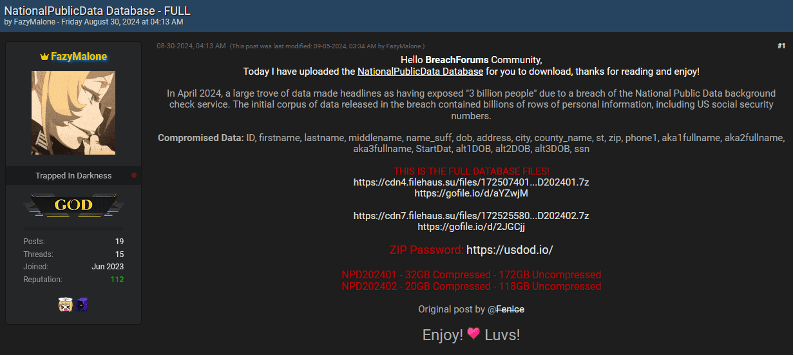
Much of the data traded for corporate access originates from well-publicized breaches or is harvested via infostealers. These infostealers, like Vidar and Redline, are frequently used to siphon login credentials from compromised devices. These credentials are then sold in bulk on underground forums or offered as part of access packages.
One prominent example is the sale of credentials linked to a breach at a North American financial institution. The listing offered RDP access to the company’s network, likely obtained through a combination of phishing and infostealer malware. Similarly, credentials linked to healthcare organizations and university networks in the U.S. and Canada have been offered for sale, highlighting how infostealers play a critical role in these underground economies.
Types of Access Sold
The most commonly sold types of access on these forums include VPN credentials, RDP access, and increasingly, cloud platform access. VPN credentials allow buyers to gain access to secure corporate networks by bypassing firewalls, while RDP access grants full control over a target machine, allowing attackers to move laterally within the system and escalate privileges.
Cloud platform access is also becoming more prevalent as companies move critical infrastructure to cloud services like AWS and Azure. Listings advertising admin access to a company’s cloud infrastructure, such as AWS environments, have attracted interest, as cloud-based environments represent a significant attack surface for organizations.
The Importance of Comprehensive Corporate Protection
Many of the cyberattacks observed on underground forums are rooted in data obtained from data breaches or infostealers, highlighting the urgent need for organizations to expand their security focus beyond traditional corporate credentials. While many companies concentrate their defenses on securing credentials from corporate devices, cybercriminals do not discriminate between data obtained from corporate or personal devices. Their sole interest is in accessing valuable data from targeted or attractive companies.
For threat actors, it doesn’t matter if credentials were compromised on a work-issued laptop or a personal device; as long as the credentials grant access to sensitive corporate systems, they are of high value. This means that companies must protect all potential entry points—both professional and personal. Employees often use the same passwords across platforms or access corporate resources from personal devices, creating a significant vulnerability.
On the other hand, there is another important issue because many organizations continue to rely heavily on Multi-Factor Authentication (MFA) and VPN solutions as their primary security mechanisms. However, recent studies, such as those by Constella Intelligence, have demonstrated that these protections are no longer as foolproof as once believed. Infostealers—malware designed to harvest login credentials and other sensitive information—have proven effective at bypassing these security measures. Threat actors can use stolen data to circumvent both MFA and VPN mechanisms, rendering them ineffective against sophisticated attacks.
In particular, infostealers can capture session tokens, cookies, and authentication tokens that allow attackers to bypass MFA entirely. Even if a corporate system requires two-factor authentication, attackers can replay these tokens to gain unauthorized access. Likewise, VPN protections can be bypassed if attackers obtain the necessary credentials and tokens, allowing them to enter corporate networks as legitimate users without raising red flags.
This growing threat underscores that, while MFA and VPNs are important components of a security strategy, they can no longer be the sole lines of defense. Organizations need to adopt more advanced security measures that address the vulnerabilities exposed by credential-based attacks.