Cyber Threats in the Age of AI: Protecting Your Digital DNA
The rapid proliferation of AI also introduces a new frontier for cyber threats against your digital DNA. As businesses and individuals increasingly adopt AI technologies, they inadvertently become prime targets for cybercriminals. The allure lies in the vast amounts of sensitive data handled by AI applications, spanning from financial records to personal information.
AI has transformed from niche technology into a mainstream powerhouse, revolutionizing industries and reshaping the way we interact with technology. From predictive analytics to autonomous vehicles, AI tools have become indispensable assets for companies seeking efficiency, innovation, and competitive advantage.
Moreover, the predominance of paid tools and services within the AI sector makes it an enticing prospect for cyber attackers seeking economic gain. Breaching AI companies provides access to valuable assets such as bank data, proprietary algorithms, and project details, while exploiting vulnerabilities in AI systems can lead to unauthorized extraction of personal information. Consequently, as we witness the expansion of the AI industry, it’s imperative for businesses and individuals to bolster their defenses against potential breaches and data compromises.
Hackers can read private Ai-assisted chats even though they are encrypted
Recently, security breaches have been reported at prominent companies in the field of Artificial Intelligence (AI), such as Cutout.pro and Leadzen.ai. These incidents have exposed a range of critical data, raising serious concerns about the protection of personal and confidential information.
Cutout.pro, founded in 2018 and based in China, is known for its innovative AI-based image processing technology. The potential attack occurred on February 28, 2024, where approximately 20M records were exposed.
Data exposed in the Cutout.pro breach:
- Email addresses
- Passwords
- Names
- Surnames
- Phone numbers
- IP addresses

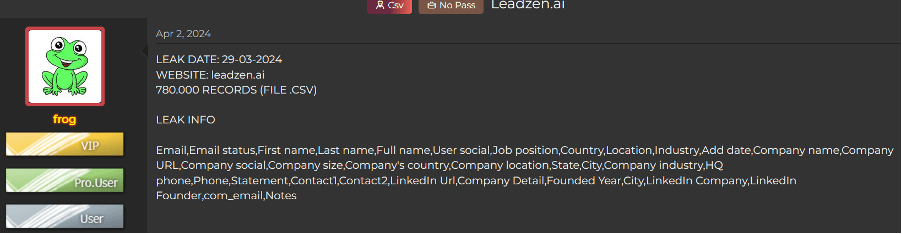
On the other hand, Leadzen.ai, established in 2020 and headquartered in India, is known for its lead generation automation platform using AI. The attack potentially happened on March 29th, 2024, and approximately 780K records were compromised.
Data exposed in the Leadzen.ai breach:
- Full Name
- User Social Networks
- Job Position
- Country
- Location
- Company Information
- Location
- Phone

The compromised data was similar to those exposed on Cutout.pro potential attack, highlighting the critical importance of cybersecurity in an ever-evolving digital environment.


These attacks underscore the urgent need for companies to strengthen their cybersecurity measures and adopt robust practices to protect the sensitive data of their users and employees. In an increasingly interconnected digital world, safeguarding personal and confidential information is crucial to ensuring trust and integrity online.
Types of Attacks and Associated Risks: Given the nature of the data exposed in the breaches at Cutout.pro and Leadzen.ai, companies must be vigilant against several types of cyber threats:
- Phishing and Spear Phishing Attacks: Cybercriminals can use the stolen email addresses and personal information to craft personalized phishing emails, tricking recipients into revealing more sensitive data or downloading malware.
- Identity Theft: With access to full names, job positions, and other personal identifiers, attackers can impersonate individuals to commit fraud or other crimes.
- Financial Fraud: Exposed financial and company information can be used to create fake accounts or authorize fraudulent transactions.
To enhance cybersecurity and protect against the risks associated with the increasing use of AI technologies, consider these three essential tips:
- Implement Multi-Factor Authentication (MFA): This adds an extra layer of security by requiring more than one form of verification to access accounts, significantly reducing the risk of unauthorized access.
- Regularly Update and Patch Systems: Keeping software and systems up to date ensures that security vulnerabilities are addressed promptly, reducing the likelihood of exploitation by cybercriminals.
- Educate and Train Users: Continuous education on the latest cyber threats and safe practices can empower individuals and employees to recognize and avoid potential cybersecurity risks, such as phishing attempts and other social engineering tactics.
As AI technologies continue to advance and become integral to various industries, they also open up new cybersecurity vulnerabilities. Recent breaches at companies like Cutout.pro and Leadzen.ai highlight the importance of stringent security measures. Adopting practices such as multi-factor authentication, regular updates and patches, and ongoing user education can significantly bolster our defenses. These steps are crucial not only for protecting sensitive data but also for preserving trust and integrity in an increasingly digital world, underscoring the need for a collective effort in enhancing our cybersecurity framework.